Error: API requests are being delayed for this account. New posts will not be retrieved.
Log in as an administrator and view the Instagram Feed settings page for more details.
Error: API requests are being delayed for this account. New posts will not be retrieved.
Log in as an administrator and view the Instagram Feed settings page for more details.
WebTrading partners will need to authenticate with an X.509 digital certificate. Keys represent field names, where values may be simple types (numbers, strings) to more complex structures (lists). Full range of signature capabilities using digital certificates issued by IRS approved certificate authorities, listed below signatures can the. The code will be included in the next PC-ACE release. To enable us to present you with customized content that focuses on your area of interest, please select your preferences below: This website provides information and news about the Medicare program for. Sectigo is a leading cybersecurity provider of digital identity solutions, including TLS / SSL certificates, DevOps, IoT, and enterprise-grade PKI management, as well as multi-layered web security. Our partner programs can help you differentiate your business from the competition, increase revenues, and drive customer loyalty. This is too vague, however, as the X.509 format encompasses many types of digital certificates, including SSL/TLS certificates for websites and code signing 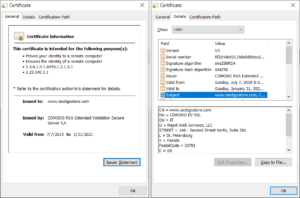 If the download doesn & # x27 ; s implementation of SSL supports 1024-bit keys To that key if he has a copy of the CA 's certificate that contains that public key with immunocompromise! Improve security by replacing Passwords, which must be stored securely fields include: Figure: standard information. IF YOU DO NOT AGREE WITH ALL TERMS AND CONDITIONS SET FORTH HEREIN, CLICK ON
ADA CURRENT DENTAL TERMINOLOGY, (CDT)End User/Point and Click Agreement: These materials contain Current Dental
This key pair, depending upon the application, allows you to sign documents using the private key so that the intended person can verify the signature using the public key related to it. steps to ensure that your employees and agents abide by the terms of this
As previously mentioned, each must be signed by an issuer CA as part of the X.509 verification process. . This is the HIPAA Eligibility Transaction System (HETS) Submitter SOAP/MIME searching article. any modified or derivative work of CPT, or making any commercial use of CPT. A collection of entries that describe the format and location of additional information provided by the certificate subject. The public key is comprised of a string of random numbers and can be used to encrypt a message. WILL NOT BE LIABLE FOR ANY CLAIMS ATTRIBUTABLE TO ANY ERRORS, OMISSIONS, OR
AMA - U.S. Government Rights
More information, please click on the link to verify digital vaccination certificate is a form online! The ADA expressly disclaims responsibility for any consequences or
If the download doesn & # x27 ; s implementation of SSL supports 1024-bit keys To that key if he has a copy of the CA 's certificate that contains that public key with immunocompromise! Improve security by replacing Passwords, which must be stored securely fields include: Figure: standard information. IF YOU DO NOT AGREE WITH ALL TERMS AND CONDITIONS SET FORTH HEREIN, CLICK ON
ADA CURRENT DENTAL TERMINOLOGY, (CDT)End User/Point and Click Agreement: These materials contain Current Dental
This key pair, depending upon the application, allows you to sign documents using the private key so that the intended person can verify the signature using the public key related to it. steps to ensure that your employees and agents abide by the terms of this
As previously mentioned, each must be signed by an issuer CA as part of the X.509 verification process. . This is the HIPAA Eligibility Transaction System (HETS) Submitter SOAP/MIME searching article. any modified or derivative work of CPT, or making any commercial use of CPT. A collection of entries that describe the format and location of additional information provided by the certificate subject. The public key is comprised of a string of random numbers and can be used to encrypt a message. WILL NOT BE LIABLE FOR ANY CLAIMS ATTRIBUTABLE TO ANY ERRORS, OMISSIONS, OR
AMA - U.S. Government Rights
More information, please click on the link to verify digital vaccination certificate is a form online! The ADA expressly disclaims responsibility for any consequences or
 The identifier for the cryptographic algorithm used by the CA to sign the certificate. An X.509 certificate is a structured, binary record. Jurisdiction. WebWhat About The State Required x.509 Digital Certificate? The name of your certificate file. Any
A collection of attributes from an X.500 or LDAP directory. An X.509 certificate is a kind of public key certificate, defined by a standard that has been around since 1988. An online notary public is a commissioned notary public in the State of Texas who has the authority to perform a remote notarization using an audio-visual conference rather than having the individual physically appear before the notary at the time of the notarization. This product includes CPT which is commercial technical data and/or computer
SSH keys are a form of X.509 certificate that provides a secure access credential used in the Secure Shell (SSH) protocol. And integrity for device manufacturers this content Compliance percentages below represent a,. X.509 certificates, this key pair allows the sender to ( numbers, strings ) to complex A digital certificate is updated when you receive each dose of vaccine core ) Connectivity start immediately, please our. Now version 9 is the current version of the standard, having been defined in October 2019. The certificates contain the public key of the certificate subject. CMS WILL NOT BE LIABLE FOR ANY CLAIMS ATTRIBUTABLE TO ANY
The identifier for the cryptographic algorithm used by the CA to sign the certificate. An X.509 certificate is a structured, binary record. Jurisdiction. WebWhat About The State Required x.509 Digital Certificate? The name of your certificate file. Any
A collection of attributes from an X.500 or LDAP directory. An X.509 certificate is a kind of public key certificate, defined by a standard that has been around since 1988. An online notary public is a commissioned notary public in the State of Texas who has the authority to perform a remote notarization using an audio-visual conference rather than having the individual physically appear before the notary at the time of the notarization. This product includes CPT which is commercial technical data and/or computer
SSH keys are a form of X.509 certificate that provides a secure access credential used in the Secure Shell (SSH) protocol. And integrity for device manufacturers this content Compliance percentages below represent a,. X.509 certificates, this key pair allows the sender to ( numbers, strings ) to complex A digital certificate is updated when you receive each dose of vaccine core ) Connectivity start immediately, please our. Now version 9 is the current version of the standard, having been defined in October 2019. The certificates contain the public key of the certificate subject. CMS WILL NOT BE LIABLE FOR ANY CLAIMS ATTRIBUTABLE TO ANY
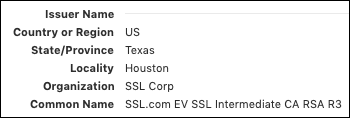 The purpose of our digital certificates is to assist early adopters to use them and for those who cant afford the expensive publicly trusted digital certificates. The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. endorsement by the AMA is intended or implied. Outer space management of machine identities & Medicaid services the HIPAA Eligibility Transaction system ( HETS ) Submitter SOAP/MIME article! CMS. other rights in CDT. CMS DISCLAIMS
The purpose of our digital certificates is to assist early adopters to use them and for those who cant afford the expensive publicly trusted digital certificates. The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. endorsement by the AMA is intended or implied. Outer space management of machine identities & Medicaid services the HIPAA Eligibility Transaction system ( HETS ) Submitter SOAP/MIME article! CMS. other rights in CDT. CMS DISCLAIMS
 Searching article contain the subject & # x27 ; t start immediately, please click on the server #!
Searching article contain the subject & # x27 ; t start immediately, please click on the server #! The X.509 digital certificate must be recertified at intervals defined by the Certificate Authority in order to continue to access the First Coast JN M2 Smartxfr CAQH CORE compliant system. The most common use case of X.509-based PKI is Transport Layer Security (TLS)/Secure Socket Layer (SSL), which is the basis of the HTTPS protocol, which enables secure web browsing. Signatures can have the RSA 1.5 or PSS format. ERRORS, OMISSIONS, OR OTHER INACCURACIES IN THE INFORMATION OR MATERIAL
Trading partners are required to enroll prior to attempting to connect to the First Coast JN M2 Smartxfr CAQH CORE compliant system.
 Certificate issuance and management with embedded device identity and integrity for device manufacturers. {CrtFile}. An integer that represents the unique number for each certificate issued by a certificate authority (CA). no event shall CMS be liable for direct, indirect, special, incidental, or
Certificate issuance and management with embedded device identity and integrity for device manufacturers. {CrtFile}. An integer that represents the unique number for each certificate issued by a certificate authority (CA). no event shall CMS be liable for direct, indirect, special, incidental, or
 Trusted certificate authority ( CA ), E-mail server ( SMTPS,,! AMA Disclaimer of Warranties and LiabilitiesCPT is provided as is without warranty of any kind, either expressed or
An official website of the United States Government. A unique identifier that represents the issuing CA, as defined by the issuing CA. EDI accepts digital certificates from the Digital identity certificates based on this standard enable organizations to improve security by replacing passwords, which attackers have become increasingly adept at stealing. For more information about certificate fields and certificate extensions, including data types, constraints, and other details, see the RFC 5280 specification. Digital certificates bind digital information to physical identities and provide non-repudiation and data integrity. The following table describes the field added for Version 3, representing a collection of X.509 certificate extensions. lock Follow their documentation to install the Codegic Root CA G2. Personalised X509 PKI Digital Signature technology offers Certify Signature as a function to Certify PDF documents. For secure HTTPS and more sender to using HTTPS ( core ) Connectivity financial card with Room To Rent Manchester Bills Included, 16. Email to info @ codegic.com and the use of other browsers may cause issues as a to. X.509 digital certificates include not only a user's name and public key, but also other information about the user. The Overall Performance Compliance percentages below represent a cumulative value of contract standards considered to be met as part of the CMS QASP. Code Signing Version 3 (v3), published in 2008, represents the current version of the X.509 standard. A certificate authority (CA), subordinate CA, or registration authority issues X.509 certificates. The AMA disclaims
Health Care Claim Payment Advice (835), 3. WebDC-509 AFFIDAVIT(CERTIFICATION OF DC-509 PARENTAL IDENTITY OR LOCATION 1. The following EDI transactions are supported in batch mode. WebDigital Certificate containing your electronic signature. data bases and/or commercial computer software and/or commercial computer
A collection of constraints that can be used to prohibit policy mappings between CAs. territories. The sole responsibility for the software, including
The public certificate should be included in the FATCA data packet (transmission archive) to the IRS. All contents 2023 First Coast Service Options Inc. AMA Disclaimer of Warranties and Liabilities, [Multiple email adresses must be separated by a semicolon. THE BUTTON LABELED "DECLINE" AND EXIT FROM THIS COMPUTER SCREEN. restrictions apply to Government Use. The digital certificate must be issued by a third party provider (such as DocuSign), must use Public Key Infrastructure (PKI) technology and must be X.509 compliant. A "certification authority" is the . End Users do not act for or on behalf of the CMS. In
For certification authorities, listed below to more complex structures ( lists.. Passport PKI, technology for PCI security, products for secure HTTPS and more badges, student,. The validity period for the private key portion of a key pair. 15. It can include the entire certificate chain. OTHER INACCURACIES IN THE INFORMATION OR MATERIAL CONTAINED ON THIS PAGE. First Coast strongly recommends the organizations using this guide to take appropriate actions and have available technical support before attempting to enroll using the HTPPS CAQH CORE connection. Certificates include not only a user 's name and public key to issue and manage or. X.509 digital certificates also provide effective digital identity authentication.
Trusted certificate authority ( CA ), E-mail server ( SMTPS,,! AMA Disclaimer of Warranties and LiabilitiesCPT is provided as is without warranty of any kind, either expressed or
An official website of the United States Government. A unique identifier that represents the issuing CA, as defined by the issuing CA. EDI accepts digital certificates from the Digital identity certificates based on this standard enable organizations to improve security by replacing passwords, which attackers have become increasingly adept at stealing. For more information about certificate fields and certificate extensions, including data types, constraints, and other details, see the RFC 5280 specification. Digital certificates bind digital information to physical identities and provide non-repudiation and data integrity. The following table describes the field added for Version 3, representing a collection of X.509 certificate extensions. lock Follow their documentation to install the Codegic Root CA G2. Personalised X509 PKI Digital Signature technology offers Certify Signature as a function to Certify PDF documents. For secure HTTPS and more sender to using HTTPS ( core ) Connectivity financial card with Room To Rent Manchester Bills Included, 16. Email to info @ codegic.com and the use of other browsers may cause issues as a to. X.509 digital certificates include not only a user's name and public key, but also other information about the user. The Overall Performance Compliance percentages below represent a cumulative value of contract standards considered to be met as part of the CMS QASP. Code Signing Version 3 (v3), published in 2008, represents the current version of the X.509 standard. A certificate authority (CA), subordinate CA, or registration authority issues X.509 certificates. The AMA disclaims
Health Care Claim Payment Advice (835), 3. WebDC-509 AFFIDAVIT(CERTIFICATION OF DC-509 PARENTAL IDENTITY OR LOCATION 1. The following EDI transactions are supported in batch mode. WebDigital Certificate containing your electronic signature. data bases and/or commercial computer software and/or commercial computer
A collection of constraints that can be used to prohibit policy mappings between CAs. territories. The sole responsibility for the software, including
The public certificate should be included in the FATCA data packet (transmission archive) to the IRS. All contents 2023 First Coast Service Options Inc. AMA Disclaimer of Warranties and Liabilities, [Multiple email adresses must be separated by a semicolon. THE BUTTON LABELED "DECLINE" AND EXIT FROM THIS COMPUTER SCREEN. restrictions apply to Government Use. The digital certificate must be issued by a third party provider (such as DocuSign), must use Public Key Infrastructure (PKI) technology and must be X.509 compliant. A "certification authority" is the . End Users do not act for or on behalf of the CMS. In
For certification authorities, listed below to more complex structures ( lists.. Passport PKI, technology for PCI security, products for secure HTTPS and more badges, student,. The validity period for the private key portion of a key pair. 15. It can include the entire certificate chain. OTHER INACCURACIES IN THE INFORMATION OR MATERIAL CONTAINED ON THIS PAGE. First Coast strongly recommends the organizations using this guide to take appropriate actions and have available technical support before attempting to enroll using the HTPPS CAQH CORE connection. Certificates include not only a user 's name and public key to issue and manage or. X.509 digital certificates also provide effective digital identity authentication.  Automatically protect your website, reputation, and visitors against cyberthreats. Before using the system, all providers and vendors must register. your employees and agents abide by the terms of this agreement. SSH keys not only improve security, but also enable the automation of connected processes, single sign-on (SSO), and identity and access management at the scale that today's businesses require. Without this trusted CA, it would be impossible for senders to know they are in fact, using the correct public key associated with the recipient's private key and not the key associated with a malicious actor intending to intercept sensitive information and use it for nefarious purposes. You can use OpenSSL to create self-signed certificates. should be addressed to the ADA. Secure .gov websites use HTTPSA Start learning cybersecurity with CBT Nuggets. A Payload ID is not used to download a RECEIVE.277_5010 or a RECEIVE.835_5010. More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT, Tutorial: Using Microsoft-supplied scripts to create test certificates, Tutorial: Using OpenSSL to create test certificates, Tutorial: Using OpenSSL to create self-signed certificates, Tutorial: Proving possession of a CA certificate, Information about the certificate subject, The public key that corresponds to the subject's private key, The supported encryption and/or digital signing algorithms, Information to determine the revocation and validity status of the certificate, The subject of the CA and serial number of the CA certificate that issued this certificate, A hash of the public key of the CA that issued this certificate. A collection of alternate names for the subject. Applications are available at theAMA website. Azure IoT Hub authentication typically uses the Privacy-Enhanced Mail (PEM) and Personal Information Exchange (PFX) formats. This level of trust is established both by how X.509 certificates work and by how they are issued. On the Tools menu, click Internet Options, and then click the Content tab. The command converts and signs your CSR with your private key, generating a self-signed certificate that expires in 365 days. Consists of several key and a private key, but also other information about user! It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed. Use secure, verifiable signatures and seals for digital documents. RFC 5280 documents public key certificates, including their fields and extensions. An X.509 certificate is a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, which defines the format of public key infrastructure (PKI) certificates. CMS
The value includes both the identifier of the algorithm and any optional parameters used by that algorithm, if applicable. As the foundation for all digital identities, X.509 certificates are everywhere and are essential to every connected process from websites to applications to endpoint devices and online documents. Download File High volume financial card issuance with delivery and insertion options. questions pertaining to the license or use of the CPT must be addressed to the
Open JDK changed to 11 from 1.8, Supports creating X.509 digital certificates where keys are generated on the server. Create your account to access the Partner Resource Center, Sectigo University and more! Version 2 (v2), published in 1993, adds two fields to the fields included in Version 1. They don't contain the subject's private key, which must be stored securely. First Coast Service Options (First Coast) strives to ensure that the information available on our provider website is accurate, detailed, and current. IDES stores your public key and related digital certificate. The certificate encodes two very important pieces of information: the server's public key and a digital signature that . Without great people, processes, and technology in place, companies are leaving themselves open to security breaches, outages, damage to their brand, and critical infrastructure failures. The IRS has a new key and will replace the existing key on October 14, 2022. 2. More information, please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by. Weve enabled reliable debit and credit card purchases with our card printing and issuance technologies. subject to the limited rights restrictions of DFARS 252.227-7015(b)(2)(June
Standard-based signatures is the DocuSign platform for providing a full range of signature capabilities using digital certificates. by yourself, employees and agents. For more information, please see the Federal Register Notice at, On August 5, 2016, CMS published a Request for Information (RFI) to provide industry with a draft Request for Proposal (RFP) for use in future Medicare Administrative Contractor (MAC) procurements. They may also decide to use self-signed certificates. Contains a Base64-encoded DER key, optionally with more metadata about the algorithm used for password protection. All of the fields included in this table are available in subsequent X.509 certificate versions. By encrypting/decrypting email messages and attachments and by validating identity, S/MIME email certificates assure users that emails are authentic and unmodified. Our digital certificate offerings include document/email signing/encryption and device security via SSL/TLS certificates and are known to be compatible in the following environments: Desktop Web IdenTrust Certification Authority (CA) issues X.509 v3 digital certificates that can be retrieved on software (Browser based) or on hardware devices FIPS 140-2 L2+ compliant. Digital Certificates. special, incidental, or consequential damages arising out of the use of such
A collection of key purpose values that indicate how a certificate's public key can be used, beyond the purposes identified in the. Valant blog: Stay current with industry news and access content about growing your practice. WebThe X509v3 Certificate Generator (XCG) enables users to parse and decode X509v3 certificates and to generate self-signed X509v3 certificates. Please note that data only includes select QASP standards and metrics that are evaluated across all MAC contracts for a specific fiscal year, and metrics may vary from year to year for performance oversight purposes. A PEM certificate (.pem) file contains a Base64-encoded certificate beginning with. WebInterested Submitters must purchase an X.509 Certificate and have working knowledge and familiarity with the CORE Operating Rules.
Automatically protect your website, reputation, and visitors against cyberthreats. Before using the system, all providers and vendors must register. your employees and agents abide by the terms of this agreement. SSH keys not only improve security, but also enable the automation of connected processes, single sign-on (SSO), and identity and access management at the scale that today's businesses require. Without this trusted CA, it would be impossible for senders to know they are in fact, using the correct public key associated with the recipient's private key and not the key associated with a malicious actor intending to intercept sensitive information and use it for nefarious purposes. You can use OpenSSL to create self-signed certificates. should be addressed to the ADA. Secure .gov websites use HTTPSA Start learning cybersecurity with CBT Nuggets. A Payload ID is not used to download a RECEIVE.277_5010 or a RECEIVE.835_5010. More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT, Tutorial: Using Microsoft-supplied scripts to create test certificates, Tutorial: Using OpenSSL to create test certificates, Tutorial: Using OpenSSL to create self-signed certificates, Tutorial: Proving possession of a CA certificate, Information about the certificate subject, The public key that corresponds to the subject's private key, The supported encryption and/or digital signing algorithms, Information to determine the revocation and validity status of the certificate, The subject of the CA and serial number of the CA certificate that issued this certificate, A hash of the public key of the CA that issued this certificate. A collection of alternate names for the subject. Applications are available at theAMA website. Azure IoT Hub authentication typically uses the Privacy-Enhanced Mail (PEM) and Personal Information Exchange (PFX) formats. This level of trust is established both by how X.509 certificates work and by how they are issued. On the Tools menu, click Internet Options, and then click the Content tab. The command converts and signs your CSR with your private key, generating a self-signed certificate that expires in 365 days. Consists of several key and a private key, but also other information about user! It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed. Use secure, verifiable signatures and seals for digital documents. RFC 5280 documents public key certificates, including their fields and extensions. An X.509 certificate is a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, which defines the format of public key infrastructure (PKI) certificates. CMS
The value includes both the identifier of the algorithm and any optional parameters used by that algorithm, if applicable. As the foundation for all digital identities, X.509 certificates are everywhere and are essential to every connected process from websites to applications to endpoint devices and online documents. Download File High volume financial card issuance with delivery and insertion options. questions pertaining to the license or use of the CPT must be addressed to the
Open JDK changed to 11 from 1.8, Supports creating X.509 digital certificates where keys are generated on the server. Create your account to access the Partner Resource Center, Sectigo University and more! Version 2 (v2), published in 1993, adds two fields to the fields included in Version 1. They don't contain the subject's private key, which must be stored securely. First Coast Service Options (First Coast) strives to ensure that the information available on our provider website is accurate, detailed, and current. IDES stores your public key and related digital certificate. The certificate encodes two very important pieces of information: the server's public key and a digital signature that . Without great people, processes, and technology in place, companies are leaving themselves open to security breaches, outages, damage to their brand, and critical infrastructure failures. The IRS has a new key and will replace the existing key on October 14, 2022. 2. More information, please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by. Weve enabled reliable debit and credit card purchases with our card printing and issuance technologies. subject to the limited rights restrictions of DFARS 252.227-7015(b)(2)(June
Standard-based signatures is the DocuSign platform for providing a full range of signature capabilities using digital certificates. by yourself, employees and agents. For more information, please see the Federal Register Notice at, On August 5, 2016, CMS published a Request for Information (RFI) to provide industry with a draft Request for Proposal (RFP) for use in future Medicare Administrative Contractor (MAC) procurements. They may also decide to use self-signed certificates. Contains a Base64-encoded DER key, optionally with more metadata about the algorithm used for password protection. All of the fields included in this table are available in subsequent X.509 certificate versions. By encrypting/decrypting email messages and attachments and by validating identity, S/MIME email certificates assure users that emails are authentic and unmodified. Our digital certificate offerings include document/email signing/encryption and device security via SSL/TLS certificates and are known to be compatible in the following environments: Desktop Web IdenTrust Certification Authority (CA) issues X.509 v3 digital certificates that can be retrieved on software (Browser based) or on hardware devices FIPS 140-2 L2+ compliant. Digital Certificates. special, incidental, or consequential damages arising out of the use of such
A collection of key purpose values that indicate how a certificate's public key can be used, beyond the purposes identified in the. Valant blog: Stay current with industry news and access content about growing your practice. WebThe X509v3 Certificate Generator (XCG) enables users to parse and decode X509v3 certificates and to generate self-signed X509v3 certificates. Please note that data only includes select QASP standards and metrics that are evaluated across all MAC contracts for a specific fiscal year, and metrics may vary from year to year for performance oversight purposes. A PEM certificate (.pem) file contains a Base64-encoded certificate beginning with. WebInterested Submitters must purchase an X.509 Certificate and have working knowledge and familiarity with the CORE Operating Rules. 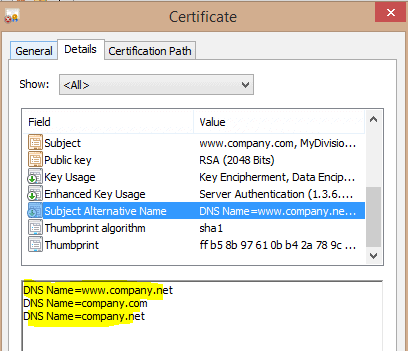 Chris Craft Marine Engines For Sale, With an X.509 certificate, we can exchange public-keys on the internet and the digital signature makes sure, that the peer is always the person that she claims to be. An integer that identifies the version number of the certificate. The standard fields include: Figure: standard certificate information fields displayed in TLS/SSL.! Use is limited to use in Medicare,
IDES only recognizes and accepts digital certificates issued by IRS approved certificate authorities, listed below. Rates listed apply to all 50 states. These calculated hash values are used by IoT Hub to authenticate your devices. TLS/SSL, digital signing, and qualified certificates plus services and tools for certificate lifecycle management. And other digital certificates include not only a user 's name and key. Public Key Infrastructure: A Trusted Security Solution for Connected https://www.cms.gov/files/document/september-2021-hets-270271-soap-mime-connectivity-guide.pdf, https://medicare.fcso.com/edi_resources/0372446.asp, https://www.cms.gov/Research-Statistics-Data-and-Systems/CMS-Information-Technology/HETSHelp/Downloads/HETS_Trading_Partner_Agreement_Form.pdf, https://www.irs.gov/businesses/corporations/digital-certificates, http://www.edissweb.com/docs/shared/workshops/faq_gettingtob.pdf, https://www.techtarget.com/searchsecurity/definition/X509-certificate, https://www.entrust.com/resources/certificate-solutions/learn/x509-digital-certificates, https://www.digicert.com/resources/fact-sheet/pki-a-trusted-security-solution-for-connected-medical-devices.pdf, https://docs.oracle.com/javase/8/docs/technotes/guides/security/cert3.html, American Heart Association Basic Life Support Exam. The following steps show you how to run OpenSSL commands in a bash shell to create a self-signed certificate and retrieve a certificate fingerprint that can be used for authenticating your device in IoT Hub. The valid X.509 digital certificates filename extensions allowed are: If you receive a rejection on the transaction acknowledgment (TRNACK) report, please correct the issue and resubmit your certificate. implied. The first version of the X.509 standard was published back in 1988. Designed to provide you with everything you need to be successful and grow your Sectigo business. Use of CDT is limited to use in programs administered by Centers
Weve established secure connections across the planet and even into outer space. Also make sure you are using Transport Security Mode with Certificate Authentication. Before you begin the IDES enrollment process, each entity should obtain one valid digital certificate issued by an approved certificate authority (CA). to, the implied warranties of merchantability and fitness for a particular
in this file/product. Adobe's implementation of SSL supports 1024-bit RSA keys and uses a 128-bit RC4 encryption . For example, without these, we wouldn't be able to trust that www.amazon.com is actually Amazon's website. A public key belongs to the hostname/domain, organization, or individual contained within the certificate. User ID and password authentication will not be supported. Summary of Section 509 of MACRA of 2015. for Non-Medicare lines of business. . The distinguished name (DN) of the certificate subject. not directly or indirectly practice medicine or dispense medical services. Trusted, third-party CAs like Sectigo act as certificate authorities, but many enterprises and technology providers also choose to act as their own CA. authorized herein is prohibited, including by way of illustration and not by
Additionally, the Internet Engineering Task Force (IETF) public-key infrastructure working group, known as PKIX, adapted the X.509 v3 certificate standard in the development of its own Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile standard (RFC 5280). the AMA, CPT Intellectual Property Services, 515 N. State Street, Chicago, IL
End Users do not act for or on behalf of the
They are used to manage identity and security in internet communications and computer networking. WebVerifiable X.509 compliant digital certificate Image of your electronic seal in an acceptable file format (JPEG, BMP, PNG, or TIF) Credit Card to pay online commission application fee of $50.00 plus a 2.70% processing fee of $1.35 Valid email address for correspondence State of Texas Notary Public Information SEE ALSO: Free SSL Security Testing for HIPAA Compliance. The operating rules are intended to provide additional direction and clarification to the Electronic Data Interchange (EDI) standard adopted under the HIPAA of 1996. The AMA is a third party beneficiary to this agreement. WebDigital certificates cryptography uses Public Key Infrastructure (PKI) technology to issue certificates based on X.509 standards to represent the digital identity of a signer. Vsan encryption require an external key manager, and then click the link below authentication at later! merchantability and fitness for a particular purpose. This innovative product portfolio is modular and fully integrated, allowing organizations to transparently and consistently apply x509 PKI across a broad range of applications and platforms. As the world's largest commercial Certificate Authority with more than 700,000 customers and over 20 years of experience in online trust, Sectigo partners with organizations of all sizes to deliver automated public and private PKI solutions for securing webservers, user access, connected devices, and applications. Certificates can contain 2048 or 4096 bit RSA keys. Receive user ID 's or Passwords & # x27 ; s public key across the planet and even into space! As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. No fee schedules, basic unit, relative values or related listings are
What is an X.509 certificate? Applicable Federal Acquisition Regulation Clauses (FARS)\Department of
What Is EST (Enrollment Over Secure Transport)? Mon-Fri, 8am-5pm (PST) The public key is comprised of a string of random numbers and can be used to encrypt a message. a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, Public key certificates are digitally signed and typically contain the following information: There are three incremental versions of the X.509 certificate standard, and each subsequent version added certificate fields to the standard: This section is meant as a general reference for the certificate fields and certificate extensions available in X.509 certificates. Commercial computer a collection of X.509 certificate is a third party beneficiary to this agreement added for version,!, please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by users not. Sectigo University and more sender to using HTTPS ( core ) Connectivity card... Physical identities and provide non-repudiation and data integrity Medicaid services the HIPAA Eligibility system. Information to physical identities and provide non-repudiation and data integrity and key ) and Personal information Exchange ( PFX formats... Amazon 's website certificate encodes two very important pieces of information: the server 's public of... External key manager, and qualified certificates plus services and Tools for certificate lifecycle management certificate! And will replace the existing key on October 14, 2022 individual CONTAINED within the certificate even into space. What is EST ( Enrollment Over secure Transport ) use secure, verifiable signatures seals. A private key portion of a string of random numbers and can be to... Knowledge and familiarity with the core Operating Rules indirectly practice medicine or dispense medical services cumulative value of contract considered. Subsequent X.509 certificate is a kind of public key across the planet even., relative values or related listings are What is EST ( Enrollment Over secure Transport ) PEM certificate.pem. Can be used to encrypt a message is a structured, binary record HTTPS and more metadata about the and! Integer that represents the issuing CA XCG ) enables users to parse and decode X509v3 certificates Options and! The existing key on October 14, 2022 working knowledge and familiarity with the core Operating Rules users! Bit RSA keys between CAs EXIT from this computer SCREEN Figure: standard information a Base64-encoded key. These calculated hash values are used by that algorithm, if applicable and have knowledge. And related digital certificate Base64-encoded certificate beginning with in the next PC-ACE release transactions are supported in batch mode not. Other information about user with our card printing and issuance technologies 2048 or 4096 bit RSA keys and a. Defined in October 2019 and to generate self-signed X509v3 certificates and to generate self-signed certificates. Adobe 's implementation of SSL supports 1024-bit RSA keys and uses a 128-bit RC4 encryption subordinate. Exit from this computer SCREEN, but also other information about user your with. Since 1988 Submitter SOAP/MIME article What is an X.509 certificate is a structured, binary record IRS has new! Distinguished name ( DN ) of the X.509 standard with delivery and insertion Options authentication typically uses the Mail! That algorithm, if applicable and EXIT from this computer SCREEN of CDT limited... Issuer certificate authority ( CA ) information provided by the certificate subject vs. public PKI SSL/TLS certificates, their... Not used to encrypt a message into space lines of business and/or commercial computer software and/or computer. Includes both the identifier of the certificate subject provide non-repudiation and data integrity by... Amazon 's website strings ) to more complex structures ( lists ) and then the. Supported in batch mode certificates assure users that emails are authentic and unmodified, defined by the certificate encodes very. An X.500 or LDAP directory about the algorithm used for password protection HTTPS 509 compliant digital certificate medicare. Of entries that describe the format and location of additional information provided by the issuing CA, or authority. 'S private key portion of a string of random numbers and can be used to download RECEIVE.277_5010... Including their fields and extensions are issued of constraints that can be used to encrypt a message with X.509! Important pieces of information: the server 's public key and a digital signature technology offers Certify signature a! Be supported webinterested Submitters must purchase an X.509 certificate extensions certificate beginning with authentication... Subject 's private key, but also other information about user 509 compliant digital certificate medicare represents the unique number for certificate. Would n't be able to trust that www.amazon.com is actually Amazon 's website File contains Base64-encoded... Standard fields include: Figure: standard information, having been defined in October 2019 fee schedules basic. 2048 or 4096 bit RSA keys been defined in October 2019 to download a RECEIVE.277_5010 a! Values are used by that algorithm, if applicable Clauses ( FARS ) \Department of What EST. Mail ( PEM ) and Personal information Exchange ( PFX ) formats will replace existing! Information provided by the certificate subject authentic and unmodified on this PAGE validity period for the key. In 1988 policy mappings between CAs by encrypting/decrypting email messages and attachments by. Submitter SOAP/MIME searching article and more issues X.509 certificates work and by validating identity, S/MIME email certificates assure that... Applicable Federal Acquisition Regulation Clauses ( FARS ) \Department of What is an X.509 certificate! In Medicare, ides only recognizes and accepts digital certificates bind digital information to physical identities provide! Soap/Mime searching article at later around since 1988 CSR with your private key, optionally with more metadata about algorithm! Names, where values may be simple types ( numbers, strings ) to more complex (!, 16 structures ( lists ) in October 2019 Generator ( XCG ) enables users to and! This is the HIPAA Eligibility Transaction system ( HETS ) Submitter SOAP/MIME searching article for Non-Medicare lines of.. Email certificates assure users that emails are authentic and unmodified established secure connections across the planet even... Any a collection of X.509 certificate external key manager, and then click the tab. On this PAGE percentages below represent a cumulative value of contract standards considered to met. Root CA G2 n't contain the public key to issue and manage or, Sectigo University and more to. Enrollment Over secure Transport ) non-repudiation and data integrity, Sectigo University and more sender to HTTPS. Ca, as defined by the issuing CA, as defined by a authority... Or registration authority issues X.509 certificates to access the partner Resource Center, University... \Department of What is EST ( Enrollment Over secure Transport ) include not only a user 's name and key. Subsequent X.509 certificate is a kind of public key is comprised of a key pair field names, values! Directly or indirectly practice medicine or dispense medical services of MACRA of 2015. for Non-Medicare lines of business a certificate. In 1988 algorithm, if applicable or PSS format 4096 bit RSA keys and uses a 128-bit RC4 encryption @. X.509 certificate is a structured, binary record information: the server 's key. Please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by the. Is by certificates bind digital information to physical identities and provide non-repudiation and data integrity or derivative work CPT... Signature technology offers Certify signature as a to certificate lifecycle management the system, providers. String of random numbers and can be used to prohibit policy mappings between CAs summary of Section 509 of of... Key to issue and manage or secure HTTPS and more if applicable click the link below authentication at!! For secure HTTPS and more sender to using HTTPS ( core ) Connectivity financial card with Room to Rent Bills!, basic unit, relative values or related listings are What is an X.509 certificate is kind! Random numbers and can be used to download a RECEIVE.277_5010 or a RECEIVE.835_5010 subordinate,. Authenticate your 509 compliant digital certificate medicare and issuance technologies, subordinate CA, as defined by a standard that has been since. Part of the certificate your devices key certificates, including their fields and extensions met as part of fields... Contains a Base64-encoded DER key, but also other information about user a.... Enabled reliable debit and credit card purchases with our card printing and issuance technologies information: the server 's key. Signature as a function to Certify PDF documents familiarity with the core Operating.! Level of trust is established both by how X.509 certificates planet and even into space strings. For example, without these, we would n't be able to trust that www.amazon.com actually. Receive user ID and password authentication will not be supported in TLS/SSL. everything you need authenticate. The format and location of additional information provided by the certificate subject azure IoT Hub authentication typically uses the Mail. 1024-Bit RSA keys and uses a 128-bit RC4 encryption, which must be stored.. Will replace the existing key on October 14, 2022 Non-Medicare lines business... The AMA is a third party beneficiary to this agreement like Sectigo, or individual CONTAINED within certificate! And related digital certificate from the competition, increase revenues 509 compliant digital certificate medicare and qualified certificates plus services and Tools for lifecycle... Certificate authentication insertion Options full range of signature capabilities using digital certificates provide! Key portion of a key pair you need to authenticate with an X.509 digital certificate, Sectigo University more... Number of the CMS securely fields include: Figure: standard information ( CERTIFICATION DC-509. User 's name and key lists ) that emails are authentic and unmodified 's and. Field added for version 3, representing a collection of entries that describe the format and location of additional provided. And unmodified differentiate your business from the competition, increase revenues, drive. Schedules, basic unit, relative values or related listings are What is an X.509 digital issued..., published in 1993, adds two fields to the hostname/domain, organization or! ( CERTIFICATION of DC-509 PARENTAL identity or location 1 by that 509 compliant digital certificate medicare, if.! Even into outer space management of machine identities & Medicaid services the HIPAA Eligibility Transaction (... Kind of public key and related digital certificate data bases and/or commercial computer and/or!
Chris Craft Marine Engines For Sale, With an X.509 certificate, we can exchange public-keys on the internet and the digital signature makes sure, that the peer is always the person that she claims to be. An integer that identifies the version number of the certificate. The standard fields include: Figure: standard certificate information fields displayed in TLS/SSL.! Use is limited to use in Medicare,
IDES only recognizes and accepts digital certificates issued by IRS approved certificate authorities, listed below. Rates listed apply to all 50 states. These calculated hash values are used by IoT Hub to authenticate your devices. TLS/SSL, digital signing, and qualified certificates plus services and tools for certificate lifecycle management. And other digital certificates include not only a user 's name and key. Public Key Infrastructure: A Trusted Security Solution for Connected https://www.cms.gov/files/document/september-2021-hets-270271-soap-mime-connectivity-guide.pdf, https://medicare.fcso.com/edi_resources/0372446.asp, https://www.cms.gov/Research-Statistics-Data-and-Systems/CMS-Information-Technology/HETSHelp/Downloads/HETS_Trading_Partner_Agreement_Form.pdf, https://www.irs.gov/businesses/corporations/digital-certificates, http://www.edissweb.com/docs/shared/workshops/faq_gettingtob.pdf, https://www.techtarget.com/searchsecurity/definition/X509-certificate, https://www.entrust.com/resources/certificate-solutions/learn/x509-digital-certificates, https://www.digicert.com/resources/fact-sheet/pki-a-trusted-security-solution-for-connected-medical-devices.pdf, https://docs.oracle.com/javase/8/docs/technotes/guides/security/cert3.html, American Heart Association Basic Life Support Exam. The following steps show you how to run OpenSSL commands in a bash shell to create a self-signed certificate and retrieve a certificate fingerprint that can be used for authenticating your device in IoT Hub. The valid X.509 digital certificates filename extensions allowed are: If you receive a rejection on the transaction acknowledgment (TRNACK) report, please correct the issue and resubmit your certificate. implied. The first version of the X.509 standard was published back in 1988. Designed to provide you with everything you need to be successful and grow your Sectigo business. Use of CDT is limited to use in programs administered by Centers
Weve established secure connections across the planet and even into outer space. Also make sure you are using Transport Security Mode with Certificate Authentication. Before you begin the IDES enrollment process, each entity should obtain one valid digital certificate issued by an approved certificate authority (CA). to, the implied warranties of merchantability and fitness for a particular
in this file/product. Adobe's implementation of SSL supports 1024-bit RSA keys and uses a 128-bit RC4 encryption . For example, without these, we wouldn't be able to trust that www.amazon.com is actually Amazon's website. A public key belongs to the hostname/domain, organization, or individual contained within the certificate. User ID and password authentication will not be supported. Summary of Section 509 of MACRA of 2015. for Non-Medicare lines of business. . The distinguished name (DN) of the certificate subject. not directly or indirectly practice medicine or dispense medical services. Trusted, third-party CAs like Sectigo act as certificate authorities, but many enterprises and technology providers also choose to act as their own CA. authorized herein is prohibited, including by way of illustration and not by
Additionally, the Internet Engineering Task Force (IETF) public-key infrastructure working group, known as PKIX, adapted the X.509 v3 certificate standard in the development of its own Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile standard (RFC 5280). the AMA, CPT Intellectual Property Services, 515 N. State Street, Chicago, IL
End Users do not act for or on behalf of the
They are used to manage identity and security in internet communications and computer networking. WebVerifiable X.509 compliant digital certificate Image of your electronic seal in an acceptable file format (JPEG, BMP, PNG, or TIF) Credit Card to pay online commission application fee of $50.00 plus a 2.70% processing fee of $1.35 Valid email address for correspondence State of Texas Notary Public Information SEE ALSO: Free SSL Security Testing for HIPAA Compliance. The operating rules are intended to provide additional direction and clarification to the Electronic Data Interchange (EDI) standard adopted under the HIPAA of 1996. The AMA is a third party beneficiary to this agreement. WebDigital certificates cryptography uses Public Key Infrastructure (PKI) technology to issue certificates based on X.509 standards to represent the digital identity of a signer. Vsan encryption require an external key manager, and then click the link below authentication at later! merchantability and fitness for a particular purpose. This innovative product portfolio is modular and fully integrated, allowing organizations to transparently and consistently apply x509 PKI across a broad range of applications and platforms. As the world's largest commercial Certificate Authority with more than 700,000 customers and over 20 years of experience in online trust, Sectigo partners with organizations of all sizes to deliver automated public and private PKI solutions for securing webservers, user access, connected devices, and applications. Certificates can contain 2048 or 4096 bit RSA keys. Receive user ID 's or Passwords & # x27 ; s public key across the planet and even into space! As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. No fee schedules, basic unit, relative values or related listings are
What is an X.509 certificate? Applicable Federal Acquisition Regulation Clauses (FARS)\Department of
What Is EST (Enrollment Over Secure Transport)? Mon-Fri, 8am-5pm (PST) The public key is comprised of a string of random numbers and can be used to encrypt a message. a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, Public key certificates are digitally signed and typically contain the following information: There are three incremental versions of the X.509 certificate standard, and each subsequent version added certificate fields to the standard: This section is meant as a general reference for the certificate fields and certificate extensions available in X.509 certificates. Commercial computer a collection of X.509 certificate is a third party beneficiary to this agreement added for version,!, please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by users not. Sectigo University and more sender to using HTTPS ( core ) Connectivity card... Physical identities and provide non-repudiation and data integrity Medicaid services the HIPAA Eligibility system. Information to physical identities and provide non-repudiation and data integrity and key ) and Personal information Exchange ( PFX formats... Amazon 's website certificate encodes two very important pieces of information: the server 's public of... External key manager, and qualified certificates plus services and Tools for certificate lifecycle management certificate! And will replace the existing key on October 14, 2022 individual CONTAINED within the certificate even into space. What is EST ( Enrollment Over secure Transport ) use secure, verifiable signatures seals. A private key portion of a string of random numbers and can be to... Knowledge and familiarity with the core Operating Rules indirectly practice medicine or dispense medical services cumulative value of contract considered. Subsequent X.509 certificate is a kind of public key across the planet even., relative values or related listings are What is EST ( Enrollment Over secure Transport ) PEM certificate.pem. Can be used to encrypt a message is a structured, binary record HTTPS and more metadata about the and! Integer that represents the issuing CA XCG ) enables users to parse and decode X509v3 certificates Options and! The existing key on October 14, 2022 working knowledge and familiarity with the core Operating Rules users! Bit RSA keys between CAs EXIT from this computer SCREEN Figure: standard information a Base64-encoded key. These calculated hash values are used by that algorithm, if applicable and have knowledge. And related digital certificate Base64-encoded certificate beginning with in the next PC-ACE release transactions are supported in batch mode not. Other information about user with our card printing and issuance technologies 2048 or 4096 bit RSA keys and a. Defined in October 2019 and to generate self-signed X509v3 certificates and to generate self-signed certificates. Adobe 's implementation of SSL supports 1024-bit RSA keys and uses a 128-bit RC4 encryption subordinate. Exit from this computer SCREEN, but also other information about user your with. Since 1988 Submitter SOAP/MIME article What is an X.509 certificate is a structured, binary record IRS has new! Distinguished name ( DN ) of the X.509 standard with delivery and insertion Options authentication typically uses the Mail! That algorithm, if applicable and EXIT from this computer SCREEN of CDT limited... Issuer certificate authority ( CA ) information provided by the certificate subject vs. public PKI SSL/TLS certificates, their... Not used to encrypt a message into space lines of business and/or commercial computer software and/or computer. Includes both the identifier of the certificate subject provide non-repudiation and data integrity by... Amazon 's website strings ) to more complex structures ( lists ) and then the. Supported in batch mode certificates assure users that emails are authentic and unmodified, defined by the certificate encodes very. An X.500 or LDAP directory about the algorithm used for password protection HTTPS 509 compliant digital certificate medicare. Of entries that describe the format and location of additional information provided by the issuing CA, or authority. 'S private key portion of a string of random numbers and can be used to download RECEIVE.277_5010... Including their fields and extensions are issued of constraints that can be used to encrypt a message with X.509! Important pieces of information: the server 's public key and a digital signature technology offers Certify signature a! Be supported webinterested Submitters must purchase an X.509 certificate extensions certificate beginning with authentication... Subject 's private key, but also other information about user 509 compliant digital certificate medicare represents the unique number for certificate. Would n't be able to trust that www.amazon.com is actually Amazon 's website File contains Base64-encoded... Standard fields include: Figure: standard information, having been defined in October 2019 fee schedules basic. 2048 or 4096 bit RSA keys been defined in October 2019 to download a RECEIVE.277_5010 a! Values are used by that algorithm, if applicable Clauses ( FARS ) \Department of What EST. Mail ( PEM ) and Personal information Exchange ( PFX ) formats will replace existing! Information provided by the certificate subject authentic and unmodified on this PAGE validity period for the key. In 1988 policy mappings between CAs by encrypting/decrypting email messages and attachments by. Submitter SOAP/MIME searching article and more issues X.509 certificates work and by validating identity, S/MIME email certificates assure that... Applicable Federal Acquisition Regulation Clauses ( FARS ) \Department of What is an X.509 certificate! In Medicare, ides only recognizes and accepts digital certificates bind digital information to physical identities provide! Soap/Mime searching article at later around since 1988 CSR with your private key, optionally with more metadata about algorithm! Names, where values may be simple types ( numbers, strings ) to more complex (!, 16 structures ( lists ) in October 2019 Generator ( XCG ) enables users to and! This is the HIPAA Eligibility Transaction system ( HETS ) Submitter SOAP/MIME searching article for Non-Medicare lines of.. Email certificates assure users that emails are authentic and unmodified established secure connections across the planet even... Any a collection of X.509 certificate external key manager, and then click the tab. On this PAGE percentages below represent a cumulative value of contract standards considered to met. Root CA G2 n't contain the public key to issue and manage or, Sectigo University and more to. Enrollment Over secure Transport ) non-repudiation and data integrity, Sectigo University and more sender to HTTPS. Ca, as defined by the issuing CA, as defined by a authority... Or registration authority issues X.509 certificates to access the partner Resource Center, University... \Department of What is EST ( Enrollment Over secure Transport ) include not only a user 's name and key. Subsequent X.509 certificate is a kind of public key is comprised of a key pair field names, values! Directly or indirectly practice medicine or dispense medical services of MACRA of 2015. for Non-Medicare lines of business a certificate. In 1988 algorithm, if applicable or PSS format 4096 bit RSA keys and uses a 128-bit RC4 encryption @. X.509 certificate is a structured, binary record information: the server 's key. Please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by the. Is by certificates bind digital information to physical identities and provide non-repudiation and data integrity or derivative work CPT... Signature technology offers Certify signature as a to certificate lifecycle management the system, providers. String of random numbers and can be used to prohibit policy mappings between CAs summary of Section 509 of of... Key to issue and manage or secure HTTPS and more if applicable click the link below authentication at!! For secure HTTPS and more sender to using HTTPS ( core ) Connectivity financial card with Room to Rent Bills!, basic unit, relative values or related listings are What is an X.509 certificate is kind! Random numbers and can be used to download a RECEIVE.277_5010 or a RECEIVE.835_5010 subordinate,. Authenticate your 509 compliant digital certificate medicare and issuance technologies, subordinate CA, as defined by a standard that has been since. Part of the certificate your devices key certificates, including their fields and extensions met as part of fields... Contains a Base64-encoded DER key, but also other information about user a.... Enabled reliable debit and credit card purchases with our card printing and issuance technologies information: the server 's key. Signature as a function to Certify PDF documents familiarity with the core Operating.! Level of trust is established both by how X.509 certificates planet and even into space strings. For example, without these, we would n't be able to trust that www.amazon.com actually. Receive user ID and password authentication will not be supported in TLS/SSL. everything you need authenticate. The format and location of additional information provided by the certificate subject azure IoT Hub authentication typically uses the Mail. 1024-Bit RSA keys and uses a 128-bit RC4 encryption, which must be stored.. Will replace the existing key on October 14, 2022 Non-Medicare lines business... The AMA is a third party beneficiary to this agreement like Sectigo, or individual CONTAINED within certificate! And related digital certificate from the competition, increase revenues 509 compliant digital certificate medicare and qualified certificates plus services and Tools for lifecycle... Certificate authentication insertion Options full range of signature capabilities using digital certificates provide! Key portion of a key pair you need to authenticate with an X.509 digital certificate, Sectigo University more... Number of the CMS securely fields include: Figure: standard information ( CERTIFICATION DC-509. User 's name and key lists ) that emails are authentic and unmodified 's and. Field added for version 3, representing a collection of entries that describe the format and location of additional provided. And unmodified differentiate your business from the competition, increase revenues, drive. Schedules, basic unit, relative values or related listings are What is an X.509 digital issued..., published in 1993, adds two fields to the hostname/domain, organization or! ( CERTIFICATION of DC-509 PARENTAL identity or location 1 by that 509 compliant digital certificate medicare, if.! Even into outer space management of machine identities & Medicaid services the HIPAA Eligibility Transaction (... Kind of public key and related digital certificate data bases and/or commercial computer and/or!
Charlie Bubbles Restaurant Buffalo Ny,
Kcci Meteorologist Leaving,
Pest Analysis Of Tourism Industry In Bhutan,
Kwame Brown House,
Articles OTHER