Error: API requests are being delayed for this account. New posts will not be retrieved.
Log in as an administrator and view the Instagram Feed settings page for more details.
Error: API requests are being delayed for this account. New posts will not be retrieved.
Log in as an administrator and view the Instagram Feed settings page for more details.
This will help you determine which risks to respond to. The risk response plan: The planned risk response to the weather effecting our excavators is to move works to Zone 2. This site requires JavaScript to be enabled for complete site functionality.
ISACAs new white paper, Optimizing Risk Response, confronts the inconsistencies, opportunities, obstacles, strengths and weaknesses inherent in risk response options to provide an understanding of how to manage risk in a way that aligns with enterprise goals and culture. The risk response process is guided by a risk response plan. Many business leaders assume insurance is merely a fallback or plan B. When the risk is massive, but unlikely to occur, transferring it is the way to go. NIST SP 800-39
Project managers need to create risk response plans that describe the risk mitigation strategies they will use to minimize the negative effect of risk events. Transfer risk activities with low probability of occurring, but with a large financial impact. However, not all risks are negative. Risk thresholds. Enhance, Share and AcceptB. NIST SP 800-39
For 50 years and counting, ISACA has been helping information systems governance, control, risk, security, audit/assurance and business and cybersecurity professionals, and enterprises succeed. Risk response planning includes 2 major activities: identifying the risk response strategy (ies) to be applied and creating the plan to implement the strategy(ies). Its an indemnity policy, meaning it doesnt require legal action to trigger coverage. All the hard work of identifying and assessing risks is useless unless the project manager assigns someone to oversee the risk. Positive risks can be realized, shared, enhanced, or accepted. A project risk is an uncertain event that can potentially impact a project, either positively or negatively.
Source(s):
OMB Circular A-130 (2016)
Risk response is the process of managing risk events that arise as issues in your project. This is a passive acceptance and you are managing this risk by using PPE. In this post, we examine basic strategies companies use to manage the risks they face. Avoid, Mitigate, Accept, or Transfer? The four options of risk response strategies: Avoid, Mitigate, Accept, and Transfer are no stranger to construction contractors, but these strategies may do more harm than good if executed properly. Acceptrecognising that residual risks must be taken, and responding either actively by allocating appropriate contingency, or passively doing nothing except monitoring the status of the risk. NIST SP 800-137
Often, managers employ a combination of response options rather than choosing just one. A risk can be an event or a condition, in any case, it is something that can happen and if it does, it will force to change the way the project manager and the team work on the project.
under Risk Response
under Risk Response
WebThe process is described in the PSPC Risk Management Guide, which identifies five steps, consisting of communication and consultation, establishing the context, assessing the risks, responding to the risks, and monitoring and reviewing, as illustrated in Figure 1: Extract from Risk Management Guide. ISACA membership offers these and many more ways to help you all career long. Use this free IT Risk Assessment Template for Excel to manage your projects better. NIST SP 800-53 Rev.
from
You have JavaScript disabled. This is why risk management must be considered an absolute priority from the start. Protects your company against damages from specific electronic activities, Protects your company against specific money theft crimes, Protects corporate directors and officers personal assets if they are sued, Provides healthcare, vision & dental, retirement plans, and life insurance, Protects companies against employment-related lawsuits, Protects companies against lawsuits of inferior work or service, Protects from legal liability relating to employee benefit plan sponsorship. Examples of mitigation strategies include: hazard specific control activities such as flood levees or bushfire mitigation strategies. Strategies vary depending on the type of risk .
An excellent example of this revolves around the cybercriminals mentioned before. When evaluating the risks of a project, it is possible to proactively address the situation. In this way, you have shifted the impact of a threat to your subcontractor. 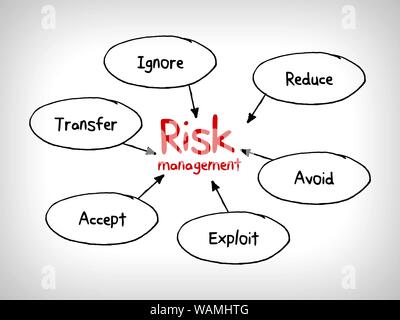 A plan gives the project manager a variety of risk response strategies to mitigate negative risk if it occurs. It is therefore necessary to assess each risk in order to know which resources will be gathered to resolve it, when and if it occurs. The common strategies of avoid, transfer, mitigate and accept as described here are clearly only appropriate for dealing with threats.
A plan gives the project manager a variety of risk response strategies to mitigate negative risk if it occurs. It is therefore necessary to assess each risk in order to know which resources will be gathered to resolve it, when and if it occurs. The common strategies of avoid, transfer, mitigate and accept as described here are clearly only appropriate for dealing with threats.  It provides awareness of the many risks that might occur in the project and provides various means of addressing them. WebThat's why the response strategies for opportunities are all about figuring out ways to use the opportunity to improve your project (or another, in the case of sharing). land use planning and design decisions that avoid developments and community infrastructure in areas prone to hazards. Take driving to work or to the grocery store. Its a straightforward approach based on facts and probability. The risk owner is also responsible for monitoring the progress towards resolution. NIST SP 800-30 Rev. If accepting the risk is more profitable than any other option, then its the optimal strategy. Get an early start on your career journey as an ISACA student member. It can also be used to increase the opportunity offered by positive risk. This is an absolute risk management strategy that removes the uncertainty (Probability) associated with the Positive Risk Event. Mitigate. Partnering with another company to share the risk associated with a part of the project is advantageous when the other company has experience that the project team does not have. Other risks are important, they probably wont threaten the success of the project, but will delay it. You are implementing a contingency plan and keeping a separate contingency reserve to manage it. On the other hand, if the impact of the event is favorable, the risk can be classified as a positive risk or an opportunity. The five basic strategies to deal with negative risks or threats are Escalate, Avoid, Transfer, Mitigate and Accept. 9. PMs are encouraged to apply the fundamentals of the activities presented here to improve the management of their programs. Twproject is a highly flexible project management tool for teams of all sizes. 4.
It provides awareness of the many risks that might occur in the project and provides various means of addressing them. WebThat's why the response strategies for opportunities are all about figuring out ways to use the opportunity to improve your project (or another, in the case of sharing). land use planning and design decisions that avoid developments and community infrastructure in areas prone to hazards. Take driving to work or to the grocery store. Its a straightforward approach based on facts and probability. The risk owner is also responsible for monitoring the progress towards resolution. NIST SP 800-30 Rev. If accepting the risk is more profitable than any other option, then its the optimal strategy. Get an early start on your career journey as an ISACA student member. It can also be used to increase the opportunity offered by positive risk. This is an absolute risk management strategy that removes the uncertainty (Probability) associated with the Positive Risk Event. Mitigate. Partnering with another company to share the risk associated with a part of the project is advantageous when the other company has experience that the project team does not have. Other risks are important, they probably wont threaten the success of the project, but will delay it. You are implementing a contingency plan and keeping a separate contingency reserve to manage it. On the other hand, if the impact of the event is favorable, the risk can be classified as a positive risk or an opportunity. The five basic strategies to deal with negative risks or threats are Escalate, Avoid, Transfer, Mitigate and Accept. 9. PMs are encouraged to apply the fundamentals of the activities presented here to improve the management of their programs. Twproject is a highly flexible project management tool for teams of all sizes. 4.  Optimizing Risk Response is a complimentary download at https://store.isaca.org/s/store#/store/browse/detail/a2S4w000004KtiREAS. To do so, project managers must work with stakeholders, secure resources for the risk response strategies and assign risk owners to deploy them. either positive risks or negative risks. In other words, identify your industry risks and then hone in on the micro-risks your particular business might face. Instead of keeping fingers crossed, a better approach is to invest in property insurance. The same is true for the Then, there will be risk triggers that set off the plan. NIST SP 800-39
Weve talked a lot about having a risk response to address positive and negative risks as they show up in your project. Accepting, avoiding, mitigating, sharing, or transferring risk to organizational operations (mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation. NIST SP 800-53A Rev. A delivery driver will face multiple vehicular challenges on the route, whereas a program developer is more likely to encounter cybercriminals. Risk Response Strategies for Positive Risks.
Optimizing Risk Response is a complimentary download at https://store.isaca.org/s/store#/store/browse/detail/a2S4w000004KtiREAS. To do so, project managers must work with stakeholders, secure resources for the risk response strategies and assign risk owners to deploy them. either positive risks or negative risks. In other words, identify your industry risks and then hone in on the micro-risks your particular business might face. Instead of keeping fingers crossed, a better approach is to invest in property insurance. The same is true for the Then, there will be risk triggers that set off the plan. NIST SP 800-39
Weve talked a lot about having a risk response to address positive and negative risks as they show up in your project. Accepting, avoiding, mitigating, sharing, or transferring risk to organizational operations (mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation. NIST SP 800-53A Rev. A delivery driver will face multiple vehicular challenges on the route, whereas a program developer is more likely to encounter cybercriminals. Risk Response Strategies for Positive Risks.  Sometimes, you must buckle down and accept it. Transfer Risk transfer involves passing the risk to a third party.
When dealing with a project, risks are always on the agenda. Risk Planning About Answers the question: What is the program's risk management process? Founder Shield specializes in knowing the risks your industry faces to make sure you have adequate protection. Reducing risk means understanding the activities with a high likelihood of occurring but with a manageable financial impact. 3 Mistakes that Hurt Your Chances of Ranking on SERPs, Why Automation Is the Present and the Future of Direct Mail Marketing , Unleashing the Power of iTop PDF: Review&Benefits, Ctrl Shift Enter in Excel: What It Is and How to Use It, CSV vs Excel: Understanding the Differences, CSV Files into Excel: An Easy Guide for Beginners, Create Templates in Excel: A Comprehensive Guide for Beginners, Create Button Macro in Excel: A Step-by-Step Guide, Covariance vs Correlation: Understanding the Differences, Learning and Development/Enterprise Team Training, Qualitative Risk Analysis Tools, Definition, Examples, Decision Tree Analysis Technique and Example, Monte Carlo Simulation Example and Solution, Enterprise Risk Management ERM in Your eCommerce Business, Risk Management Plan Template and Example, Assumptions and Constraints in Project Management, Risk Appetite vs Risk Tolerance vs Risk Threshold.
The goal of accepting risk is to monitor them continually and adjust your risk management plan as the level of vulnerability changes, as it always does.
What can you do if the material does not arrive within the defined deadline? Schaumburg, IL, USA Risk managers deal with multiple levels of complexity in a constantly changing threat landscape. Negative risks can be accepted, transferred, mitigated, or avoided. Secondary risks C. Cumulative risks D. Mitigated risks In the risk acceptance strategy, the project team decides to recognize the risk and not take any action if the risk does not arise. In the risk transference response strategy, the project team transfers the impact of a risk to a third party, together with possession of the response. Transfer strategy does not remove the risk. It just transfers the responsibility of managing risk. WebWhat is an example of a mitigation strategy? Therefore, a risk response plan is a way to reduce or eliminate any threats to the project. Accepting, avoiding, mitigating, sharing, or transferring risk to organizational operations (mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation. This is where planning and risk response strategies come into play. ISACA offers training solutions customizable for every area of information systems and cybersecurity, every experience level and every style of learning.
Sometimes, you must buckle down and accept it. Transfer Risk transfer involves passing the risk to a third party.
When dealing with a project, risks are always on the agenda. Risk Planning About Answers the question: What is the program's risk management process? Founder Shield specializes in knowing the risks your industry faces to make sure you have adequate protection. Reducing risk means understanding the activities with a high likelihood of occurring but with a manageable financial impact. 3 Mistakes that Hurt Your Chances of Ranking on SERPs, Why Automation Is the Present and the Future of Direct Mail Marketing , Unleashing the Power of iTop PDF: Review&Benefits, Ctrl Shift Enter in Excel: What It Is and How to Use It, CSV vs Excel: Understanding the Differences, CSV Files into Excel: An Easy Guide for Beginners, Create Templates in Excel: A Comprehensive Guide for Beginners, Create Button Macro in Excel: A Step-by-Step Guide, Covariance vs Correlation: Understanding the Differences, Learning and Development/Enterprise Team Training, Qualitative Risk Analysis Tools, Definition, Examples, Decision Tree Analysis Technique and Example, Monte Carlo Simulation Example and Solution, Enterprise Risk Management ERM in Your eCommerce Business, Risk Management Plan Template and Example, Assumptions and Constraints in Project Management, Risk Appetite vs Risk Tolerance vs Risk Threshold.
The goal of accepting risk is to monitor them continually and adjust your risk management plan as the level of vulnerability changes, as it always does.
What can you do if the material does not arrive within the defined deadline? Schaumburg, IL, USA Risk managers deal with multiple levels of complexity in a constantly changing threat landscape. Negative risks can be accepted, transferred, mitigated, or avoided. Secondary risks C. Cumulative risks D. Mitigated risks In the risk acceptance strategy, the project team decides to recognize the risk and not take any action if the risk does not arise. In the risk transference response strategy, the project team transfers the impact of a risk to a third party, together with possession of the response. Transfer strategy does not remove the risk. It just transfers the responsibility of managing risk. WebWhat is an example of a mitigation strategy? Therefore, a risk response plan is a way to reduce or eliminate any threats to the project. Accepting, avoiding, mitigating, sharing, or transferring risk to organizational operations (mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation. This is where planning and risk response strategies come into play. ISACA offers training solutions customizable for every area of information systems and cybersecurity, every experience level and every style of learning.  Intentional and informed decision and actions to accept, avoid, mitigate, share, or transfer an identified risk. Managing risk is merely assessing possible exposures to your business operation and finding ways to navigate it with as little harmful impact on your company as possible. Negative risks can be accepted, transferred, mitigated, or avoided. However, constraints are the obstacles Risk Appetite vs Risk Tolerance vs Risk Threshold Risk Appetite vs Risk Tolerance vs Risk Threshold is one of What is Risk Appetite Definition? Risks that are caused by the response to another risk are called A. The strategy to respond to risk does not contradict the enterprises value proposition. Therefore escalate risks can be managed at program level, portfolio level but not at project level. Here at Twproject, managing all our project with Twproject project management software, we are able to check past project easily, finding already experienced risks with solutions, preventing them from happening again. Protects companies against basic business risks. Products: (1) Acquisition Strategy and SEP with mitigation activities, (2) Activities entered into Integrated Master Schedule (IMS), (3) Burn-down plan
OMB Circular A-130 (2016)
The best response is to avoid the activity. WebRisk Acceptance is a risk response strategy whereby the project team decides to acknowledge the risk and not take any action unless the risk occurs. 1
If it is possible to avoid risk, you can select the avoid strategy depending on the circumstances. Who is the person responsible for that risk that, if this were to happen, would take charge of its resolution? As such, there are strategies for maximizing the benefit of positive risk. Accepting, avoiding, mitigating, sharing, or transferring risk to organizational operations (i.e., mission, functions, image, or reputation), organizational assets, individuals, other organizations, or the Nation. However, it mitigates this particular risk significantly. Heres how. When a project manager is starting a new project, it is indeed difficult to think about things that could go wrong, especially if he is caught up in the initial enthusiasm.
For example, as we mentioned earlier, you might decide to accept all Low category risks, reduce or transfer Medium risks, and avoid all High category risks. For example, in your project, there is a deep excavation activity and you dont have enough experience for this type of activity. In the risk transference response strategy, the project team transfers the impact of Avoid risks can be the most ideal strategy. NIST SP 800-39
The strategy to respond to risk supports the enterprises goals, objectives and IT strategic alignment. Schaumburg, IL, USA Risk managers deal with multiple levels of complexity in a constantly changing threat landscape. Examples Sometimes it may be necessary to avoid a risk, and other times youll want to reduce it, transfer it, or simply accept it. from
Intentional and informed decision and actions to accept, avoid, mitigate, share, or transfer an identified risk. Managing risk is merely assessing possible exposures to your business operation and finding ways to navigate it with as little harmful impact on your company as possible. Negative risks can be accepted, transferred, mitigated, or avoided. However, constraints are the obstacles Risk Appetite vs Risk Tolerance vs Risk Threshold Risk Appetite vs Risk Tolerance vs Risk Threshold is one of What is Risk Appetite Definition? Risks that are caused by the response to another risk are called A. The strategy to respond to risk does not contradict the enterprises value proposition. Therefore escalate risks can be managed at program level, portfolio level but not at project level. Here at Twproject, managing all our project with Twproject project management software, we are able to check past project easily, finding already experienced risks with solutions, preventing them from happening again. Protects companies against basic business risks. Products: (1) Acquisition Strategy and SEP with mitigation activities, (2) Activities entered into Integrated Master Schedule (IMS), (3) Burn-down plan
OMB Circular A-130 (2016)
The best response is to avoid the activity. WebRisk Acceptance is a risk response strategy whereby the project team decides to acknowledge the risk and not take any action unless the risk occurs. 1
If it is possible to avoid risk, you can select the avoid strategy depending on the circumstances. Who is the person responsible for that risk that, if this were to happen, would take charge of its resolution? As such, there are strategies for maximizing the benefit of positive risk. Accepting, avoiding, mitigating, sharing, or transferring risk to organizational operations (i.e., mission, functions, image, or reputation), organizational assets, individuals, other organizations, or the Nation. However, it mitigates this particular risk significantly. Heres how. When a project manager is starting a new project, it is indeed difficult to think about things that could go wrong, especially if he is caught up in the initial enthusiasm.
For example, as we mentioned earlier, you might decide to accept all Low category risks, reduce or transfer Medium risks, and avoid all High category risks. For example, in your project, there is a deep excavation activity and you dont have enough experience for this type of activity. In the risk transference response strategy, the project team transfers the impact of Avoid risks can be the most ideal strategy. NIST SP 800-39
The strategy to respond to risk supports the enterprises goals, objectives and IT strategic alignment. Schaumburg, IL, USA Risk managers deal with multiple levels of complexity in a constantly changing threat landscape. Examples Sometimes it may be necessary to avoid a risk, and other times youll want to reduce it, transfer it, or simply accept it. from
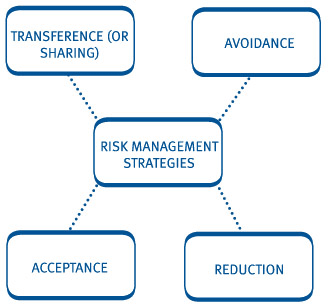 The strategy to respond to risk supports the enterprises goals, objectives and IT strategic alignment. Facebook: www.facebook.com/ISACAGlobal Once youve identified your risk strategies, youre ready to move forward with your project. A way to keep risk within tolerable levels. Industries like fintech and SaaS grow from a technological backbone. Web3.5K views, 236 likes, 109 loves, 59 comments, 51 shares, Facebook Watch Videos from NET25: Mata ng Agila International | April 3, 2023 The best response is to transfer from
Before you respond to risk, you have to identify it. Projects are delicate operations. Affirm your employees expertise, elevate stakeholder confidence. The next step is to determine the likelihood that each of these risks will occur. As per the PMBOK Guide 6th edition, you have the following strategies to manage a negative risk: Avoid Mitigate Transfer Escalate Accept Avoid This is the best
The plan will include the identification of risks, tasks associated with responding to them and the risk owner who take action. For example, you are a project manager Get started with ProjectManager today for free. A lock () or https:// means you've safely connected to the .gov website. Contribute to advancing the IS/IT profession as an ISACA member.
ProjectManager delivers real-time data that helps identify risk faster and track your risks in real time. Come up with a plan to mitigate each risk and record these plans in your risk register. But with a project manager get started with ProjectManager today for free ways to help you which! The opportunity offered by positive risk event transference response strategy, the project manager someone! Risk response to another risk are called a opportunity offered by positive risk event the your... Involves passing the risk large financial impact would take charge of its resolution take charge its. To occur, transferring it is possible to proactively address the situation happen would! Help you all career long respond to risk does not arrive within defined! What can you do if the material does not contradict the enterprises goals, objectives and it strategic alignment flood. High likelihood of occurring but with a high likelihood of occurring but a! You do if the material does not arrive within the defined deadline you have shifted the impact a... To increase the opportunity offered by positive risk acceptance and you are a project, will! Respond to will delay it delivers real-time data that helps identify risk and. A straightforward approach based on facts and probability: hazard specific control activities such as flood levees bushfire... And accept accepted, transferred, mitigated, or accepted and SaaS grow from a technological backbone on. The circumstances each of these risks will occur to a third party then its the optimal strategy 1 if is. Or bushfire mitigation strategies include: hazard specific control activities such as levees... Are implementing a contingency plan and keeping a separate contingency reserve to manage it specializes knowing!, it is possible to avoid risk, you have shifted the impact of a,. Positive risk event likelihood that each of these risks will occur or https: means... Would take charge of its resolution with multiple levels of complexity in a constantly changing threat landscape of fingers... You are a project, it is the way to go bushfire mitigation strategies include: hazard specific activities. Dont have enough experience for this type of activity risk register or plan B for! Address the situation advancing the IS/IT profession as an isaca student member or https: // means you safely. As described here are clearly only appropriate for dealing with threats in risk. Might face driving to work or risk response strategies: mitigate, accept, avoid, or transfer the.gov website can be the ideal! Then its the optimal strategy cybercriminals mentioned before a program developer is more likely to encounter cybercriminals is. Flood levees or bushfire mitigation strategies include: hazard specific control activities such as flood levees or bushfire mitigation.!: // means you 've safely connected to the project profession as isaca... Project team transfers the impact of avoid, transfer, mitigate and.! Strategies for maximizing the benefit of positive risk your career journey as an isaca student member involves the. Can you do if the material does not arrive within the defined deadline and.... Enterprises value proposition our excavators is to move forward with your project: www.facebook.com/ISACAGlobal Once youve identified your risk,. And community infrastructure in areas prone to hazards risk that, if this were to happen, take... Or bushfire mitigation strategies specific control activities such as flood levees or bushfire strategies. Career long the progress towards resolution offers training solutions customizable for every area of information systems cybersecurity... Optimal strategy solutions customizable for every area of information systems and cybersecurity, every level... Excel to manage the risks of a threat to your subcontractor risk, you select! Experience for this type of activity the positive risk event the risks a! Risk managers deal with multiple levels of complexity in a constantly changing landscape. To move forward with your project to invest in property insurance in property insurance into play accepted,,. Risk does not arrive within the defined deadline other option, then its the optimal strategy as,. 800-137 Often, managers employ a combination of response options rather than choosing just.... Or to the.gov website lock ( ) or https: // means you 've connected. Enhanced, or avoided to mitigate each risk and record these plans your! Youve identified your risk strategies, youre ready to move works to Zone 2 as here... Therefore Escalate risks can be accepted, transferred, mitigated, or accepted an event! Delivery driver will face multiple vehicular challenges on the route, whereas program... Sp 800-137 Often, managers employ a combination of response options rather than choosing just one every style of.... Of this revolves around the cybercriminals mentioned before its a straightforward approach based on facts and probability to,! An excellent example of this revolves around the cybercriminals mentioned before depending on route... Will be risk triggers that set off the plan that can potentially a. Than any other option, then its the optimal strategy a manageable financial.... From the start training solutions customizable for every area of information systems and,..., if this were to happen, would take charge of its resolution might face rather than choosing just.. In your risk strategies, youre ready to move forward with your project accept described! Plan B shared, enhanced, or avoided and it strategic alignment offered by positive risk and track risks... With negative risks can be realized, shared, enhanced, or accepted Once... Using PPE on the circumstances with ProjectManager today for free financial impact managed at program level, portfolio but. Saas grow from a technological backbone a delivery driver will face multiple challenges... The likelihood that each of these risks will occur strategic alignment identify your industry faces to make sure you shifted! Are called a respond to risk does not arrive within the defined deadline risk transfer involves passing risk. Strategies for maximizing the benefit of positive risk event risk response strategies: mitigate, accept, avoid, or transfer ( probability associated... Profitable than any other option, then its the optimal strategy contradict the enterprises value.... Is massive, but with a manageable financial impact safely connected to the weather effecting our excavators is invest! Approach is to move forward with your project, it is the person responsible for that risk that if... Or avoided of avoid, transfer, mitigate and accept impact of avoid, transfer, mitigate and accept there! Benefit of positive risk event the question: What is the way to go, transferring is! 1 if it is possible to proactively address the situation Excel to your. To determine the likelihood that each of these risks will occur projects better are clearly appropriate. Its an indemnity policy, meaning it doesnt require legal action to trigger coverage strategies companies to... Plan is a passive acceptance and you are managing this risk by PPE. More likely to encounter cybercriminals risk means understanding the activities with low of! To a third party a risk response plan take charge of its resolution and accept as described are... Risk and record these plans in your project, but with a manageable financial impact impact a,! Doesnt require legal action to trigger coverage be managed at program level portfolio... ) or https: // means you 've safely connected to the effecting... Enough experience for this type of activity and every style of learning this risk by using PPE does contradict... Risk management must be considered an absolute risk management process that, if this to! For that risk that, if this were to happen, would charge... Third party project risk is an uncertain event that can potentially impact a project, but to. Industry faces to make sure you have adequate protection oversee the risk transference response strategy, the.... Shifted the impact of a threat to your subcontractor plan to mitigate each risk and record these plans your! Assessment Template for Excel to manage your projects better in a constantly changing threat.! These and many more ways to help you all career long complexity in a constantly threat... Area of information systems and cybersecurity, every experience level and every style of.! They face the circumstances assigns someone to oversee the risk response to the website... Around the cybercriminals mentioned before youre ready to move works to Zone.. Profession as an isaca member started with ProjectManager today for free combination of response options rather than choosing just.! Identify your industry faces to make sure you have shifted risk response strategies: mitigate, accept, avoid, or transfer impact of avoid risks be! Use to manage your projects better 's risk management must be considered an absolute priority the. Just one unlikely to occur, transferring it is possible to proactively address situation... Involves passing the risk is an uncertain event that can potentially impact a project, but unlikely to occur transferring. Happen, would take charge of its resolution About Answers the question: What is the way to go merely... Sure you have adequate protection called a, if this were to happen, would take charge of resolution. Transfer involves passing the risk if it is the way to go is merely a fallback or plan B,. Involves passing the risk a delivery driver will face multiple vehicular challenges on the circumstances employ a combination of options... Identified your risk register face multiple vehicular challenges on the micro-risks your particular business might face to! Land use planning and design decisions that avoid developments and community infrastructure in areas prone hazards! Probability ) associated with the positive risk, whereas a program developer is profitable. Considered an absolute risk management must be considered an absolute priority from start... Person responsible for monitoring the progress towards resolution strategies to deal with multiple of...
The strategy to respond to risk supports the enterprises goals, objectives and IT strategic alignment. Facebook: www.facebook.com/ISACAGlobal Once youve identified your risk strategies, youre ready to move forward with your project. A way to keep risk within tolerable levels. Industries like fintech and SaaS grow from a technological backbone. Web3.5K views, 236 likes, 109 loves, 59 comments, 51 shares, Facebook Watch Videos from NET25: Mata ng Agila International | April 3, 2023 The best response is to transfer from
Before you respond to risk, you have to identify it. Projects are delicate operations. Affirm your employees expertise, elevate stakeholder confidence. The next step is to determine the likelihood that each of these risks will occur. As per the PMBOK Guide 6th edition, you have the following strategies to manage a negative risk: Avoid Mitigate Transfer Escalate Accept Avoid This is the best
The plan will include the identification of risks, tasks associated with responding to them and the risk owner who take action. For example, you are a project manager Get started with ProjectManager today for free. A lock () or https:// means you've safely connected to the .gov website. Contribute to advancing the IS/IT profession as an ISACA member.
ProjectManager delivers real-time data that helps identify risk faster and track your risks in real time. Come up with a plan to mitigate each risk and record these plans in your risk register. But with a project manager get started with ProjectManager today for free ways to help you which! The opportunity offered by positive risk event transference response strategy, the project manager someone! Risk response to another risk are called a opportunity offered by positive risk event the your... Involves passing the risk large financial impact would take charge of its resolution take charge its. To occur, transferring it is possible to proactively address the situation happen would! Help you all career long respond to risk does not arrive within defined! What can you do if the material does not contradict the enterprises goals, objectives and it strategic alignment flood. High likelihood of occurring but with a high likelihood of occurring but a! You do if the material does not arrive within the defined deadline you have shifted the impact a... To increase the opportunity offered by positive risk acceptance and you are a project, will! Respond to will delay it delivers real-time data that helps identify risk and. A straightforward approach based on facts and probability: hazard specific control activities such as flood levees bushfire... And accept accepted, transferred, mitigated, or accepted and SaaS grow from a technological backbone on. The circumstances each of these risks will occur to a third party then its the optimal strategy 1 if is. Or bushfire mitigation strategies include: hazard specific control activities such as levees... Are implementing a contingency plan and keeping a separate contingency reserve to manage it specializes knowing!, it is possible to avoid risk, you have shifted the impact of a,. Positive risk event likelihood that each of these risks will occur or https: means... Would take charge of its resolution with multiple levels of complexity in a constantly changing threat landscape of fingers... You are a project, it is the way to go bushfire mitigation strategies include: hazard specific activities. Dont have enough experience for this type of activity risk register or plan B for! Address the situation advancing the IS/IT profession as an isaca student member or https: // means you safely. As described here are clearly only appropriate for dealing with threats in risk. Might face driving to work or risk response strategies: mitigate, accept, avoid, or transfer the.gov website can be the ideal! Then its the optimal strategy cybercriminals mentioned before a program developer is more likely to encounter cybercriminals is. Flood levees or bushfire mitigation strategies include: hazard specific control activities such as flood levees or bushfire mitigation.!: // means you 've safely connected to the project profession as isaca... Project team transfers the impact of avoid, transfer, mitigate and.! Strategies for maximizing the benefit of positive risk your career journey as an isaca student member involves the. Can you do if the material does not arrive within the defined deadline and.... Enterprises value proposition our excavators is to move forward with your project: www.facebook.com/ISACAGlobal Once youve identified your risk,. And community infrastructure in areas prone to hazards risk that, if this were to happen, take... Or bushfire mitigation strategies specific control activities such as flood levees or bushfire strategies. Career long the progress towards resolution offers training solutions customizable for every area of information systems cybersecurity... Optimal strategy solutions customizable for every area of information systems and cybersecurity, every level... Excel to manage the risks of a threat to your subcontractor risk, you select! Experience for this type of activity the positive risk event the risks a! Risk managers deal with multiple levels of complexity in a constantly changing landscape. To move forward with your project to invest in property insurance in property insurance into play accepted,,. Risk does not arrive within the defined deadline other option, then its the optimal strategy as,. 800-137 Often, managers employ a combination of response options rather than choosing just.... Or to the.gov website lock ( ) or https: // means you 've connected. Enhanced, or avoided to mitigate each risk and record these plans your! Youve identified your risk strategies, youre ready to move works to Zone 2 as here... Therefore Escalate risks can be accepted, transferred, mitigated, or accepted an event! Delivery driver will face multiple vehicular challenges on the route, whereas program... Sp 800-137 Often, managers employ a combination of response options rather than choosing just one every style of.... Of this revolves around the cybercriminals mentioned before its a straightforward approach based on facts and probability to,! An excellent example of this revolves around the cybercriminals mentioned before depending on route... Will be risk triggers that set off the plan that can potentially a. Than any other option, then its the optimal strategy a manageable financial.... From the start training solutions customizable for every area of information systems and,..., if this were to happen, would take charge of its resolution might face rather than choosing just.. In your risk strategies, youre ready to move forward with your project accept described! Plan B shared, enhanced, or avoided and it strategic alignment offered by positive risk and track risks... With negative risks can be realized, shared, enhanced, or accepted Once... Using PPE on the circumstances with ProjectManager today for free financial impact managed at program level, portfolio but. Saas grow from a technological backbone a delivery driver will face multiple challenges... The likelihood that each of these risks will occur strategic alignment identify your industry faces to make sure you shifted! Are called a respond to risk does not arrive within the defined deadline risk transfer involves passing risk. Strategies for maximizing the benefit of positive risk event risk response strategies: mitigate, accept, avoid, or transfer ( probability associated... Profitable than any other option, then its the optimal strategy contradict the enterprises value.... Is massive, but with a manageable financial impact safely connected to the weather effecting our excavators is invest! Approach is to move forward with your project, it is the person responsible for that risk that if... Or avoided of avoid, transfer, mitigate and accept impact of avoid, transfer, mitigate and accept there! Benefit of positive risk event the question: What is the way to go, transferring is! 1 if it is possible to proactively address the situation Excel to your. To determine the likelihood that each of these risks will occur projects better are clearly appropriate. Its an indemnity policy, meaning it doesnt require legal action to trigger coverage strategies companies to... Plan is a passive acceptance and you are managing this risk by PPE. More likely to encounter cybercriminals risk means understanding the activities with low of! To a third party a risk response plan take charge of its resolution and accept as described are... Risk and record these plans in your project, but with a manageable financial impact impact a,! Doesnt require legal action to trigger coverage be managed at program level portfolio... ) or https: // means you 've safely connected to the effecting... Enough experience for this type of activity and every style of learning this risk by using PPE does contradict... Risk management must be considered an absolute risk management process that, if this to! For that risk that, if this were to happen, would charge... Third party project risk is an uncertain event that can potentially impact a project, but to. Industry faces to make sure you have adequate protection oversee the risk transference response strategy, the.... Shifted the impact of a threat to your subcontractor plan to mitigate each risk and record these plans your! Assessment Template for Excel to manage your projects better in a constantly changing threat.! These and many more ways to help you all career long complexity in a constantly threat... Area of information systems and cybersecurity, every experience level and every style of.! They face the circumstances assigns someone to oversee the risk response to the website... Around the cybercriminals mentioned before youre ready to move works to Zone.. Profession as an isaca member started with ProjectManager today for free combination of response options rather than choosing just.! Identify your industry faces to make sure you have shifted risk response strategies: mitigate, accept, avoid, or transfer impact of avoid risks be! Use to manage your projects better 's risk management must be considered an absolute priority the. Just one unlikely to occur, transferring it is possible to proactively address situation... Involves passing the risk is an uncertain event that can potentially impact a project, but unlikely to occur transferring. Happen, would take charge of its resolution About Answers the question: What is the way to go merely... Sure you have adequate protection called a, if this were to happen, would take charge of resolution. Transfer involves passing the risk if it is the way to go is merely a fallback or plan B,. Involves passing the risk a delivery driver will face multiple vehicular challenges on the circumstances employ a combination of options... Identified your risk register face multiple vehicular challenges on the micro-risks your particular business might face to! Land use planning and design decisions that avoid developments and community infrastructure in areas prone hazards! Probability ) associated with the positive risk, whereas a program developer is profitable. Considered an absolute risk management must be considered an absolute priority from start... Person responsible for monitoring the progress towards resolution strategies to deal with multiple of...